|
|
|
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|
|
|
|
|
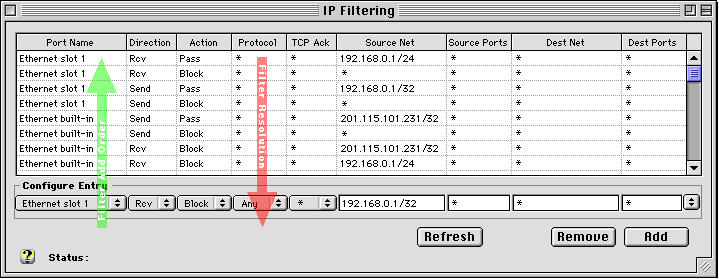
The first filter PASSes all packets RECEIVED on our slot 1 ethernet port which originated from our private subnet (only machines in our 192.168.0.1/24 subnet). | Net Result of Filters 1 & 2: Only client machines connected through the slot 1 port within our designated 192.168.0.1/24 subnet can use the IPNetRouter gateway. |
|
|
2nd Filter: All other RECEIVED packets on this slot 1 interface are BLOCKed. | |
|
|
||
|
|
3rd Filter: This filter PASSes all packets SENT from the gateway onto the private LAN. | Net Result of Filters 3 & 4: Only packets originating from the gateway machine can be SENT out to our client machines. |
|
|
4th Filter: All other packets SENT out of the gateway onto the private LAN to any other machine are BLOCKed. | |
|
|
||
|
|
5th Filter: This filter permits the gateway machine to SEND packets out to the Internet over the built-in ethernet port. | Net Result of Filters 5 & 6: Only packets originating from the gateway machine can be SENT out to the Internet. |
|
|
Filter: All other packets SENT out of the gateway to the Internet are BLOCKed. | |
|
|
||
|
|
This filter BLOCKs all packets from the Internet which claim to originate from the same IP address as our gateway. | Net Result of Filter 7: Our gateway has a unique, public IP address. No other packets received should have this same IP address...if so, BLOCK them. |
|
|
||
|
|
This filter BLOCKs any packets received from the public Internet that claim to originate from our private LAN (192.168.0.1/24) | Net Result of Filter 8: Our private subnet is strictly reserved to be used by client machines connected through the Slot 1 interface. All external attempts to use the gateway from a machine on the Internet and having an IP address within our private subnet will be BLOCKed. |
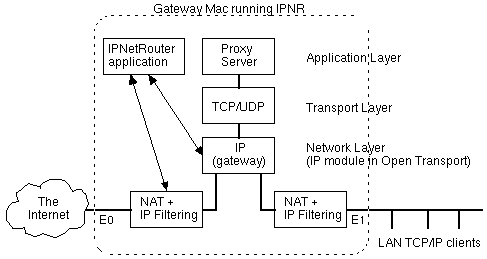
Filtering is performed before Network Address Translation (NAT) for transmitted datagrams, and after NAT for received datagrams. This allows you to filter on the "Actual LAN Address" as opposed to the "Apparent Gateway Address".
A More Practical Firewall for a Static IP Gateway
If you carefully followed the example above, you will note that this is an absolute firewall. Not only will it prevent outside users from getting in to your LAN, but it will also prevent any client machines from getting out to the Internet! This is the way most good network administrators start building a firewall:
1. First prevent all access.
2. Then permit any specific access on a case by case basis (commonly called "punching holes in a firewall").
Most users of IPNetRouter, however, want all client machines to have access to the Internet, while preventing any intrusions into their client machines or unauthorized use of their router. If you followed the example above, and understand the net results of invoking all of the eight filters, you will see that the way to let the client machines access the Internet is to remove filter lines 3, 4, 5 and 6 of the above example.
This is what the IP Filtering window would look like (once again assuming the fixed IP address you have been assigned is 201.115.101.231):

A More Practical Firewall for users with a Dynamic IP Address
Cable and DSL modem users are often assigned a dynamic IP address (through DHCP from their ISP), but still want the protection of a firewall while letting all their client machines access to the Internet. In this case, we simply replace the filter with the fixed IP address (second line from the bottom) with an entry for a dynamic IP address. To do this, just enter 0.0.0.1/32 in the Source Net edit box. Your IP Filtering window should appear similar to this:
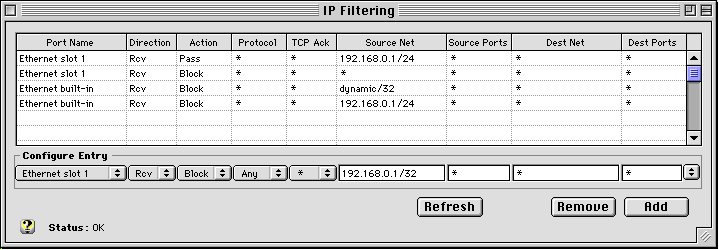
Note that the 0.0.0.1 address is replaced by the word "dynamic" in IPNetRouter's Interface.
Passing DHCP with LAN IP Filtering
If you are using the DHCP server within IPNetRouter to dynamically assign IP addresses on your private LAN, then you have to add yet one more PASS filter to any of the above examples. The reason is that we are BLOCKING all incoming packets into the Slot 1 ethernet interface which are not originating from the local 192.168.0.1/24 subnet...and our client machines do not yet have an IP address in this subnet range (remember, these client machines are using DHCP to get an IP address assigned to them).
To remedy this, we add the following filter which permits incoming DHCP discover and request messages:
![]()
This filter PASSes all UDP protocol port 68 messages (DHCP negotiation messages) which are received on our internal ethernet interface (see above for full example) so that the DHCP server within IPNetRouter can handle them.
Passing "Local NAT" with LAN IP Filtering
If you are using the optional "Enable Local NAT" feature of IPNetRouter to access a server behind your gateway using its public IP address, then you have to add yet one more PASS filter to any of the above examples. The reason is that we are BLOCKING all incoming packets into the Slot 1 (LAN) ethernet interface which are not originating from the local 192.168.0.1/24 subnet...but the Local NAT function is translating packets to the gateways public address to appear as if they originate from the gateways public address (201.115.101.231/32 or dynamic/32) so the response can be routed back correctly. This translation occurs before IP filtering for incoming packets, so the packets appear to originate from outside our LAN.
To remedy this, we add the following filter which permits Enable Local NAT to function normally:
![]()
Or, if our public IP address is static, we could also use the following filter:
![]()
Blocking Gateway Spoofing Inside the LAN
There is a filter which can be added to the top of each of the above examples which will even further secure your private LAN. Most of the time this is not necessary, since most users of IPNetRouter are also the administrator of their own small private LAN. This filter simply ensures that no one else on the private LAN is claiming to be the gateway machine (which is not an easy thing to do anyway...since you would have to spoof packets). This filter would look like this:
![]()
With this filter, all packets RECEIVED on the slot 1 interface and claiming to be from 192.168.0.1 (our IPNetRouter address) would be BLOCKed.
But, as mentioned previously, if you are in control of all the machines on your private LAN, there is very little use or need for this additional filter.
Order of NAT, Filtering, and Routing
Proxy instance Proxy instance
Internet <---> NAT <-> Filtering <---> IP <---> Filtering <-> NAT <---> LAN
Consider a packet travelling from the Internet to the LAN (left to right). Following the diagram above the order of processing is:
- Packet originates from Internet
- NAT on Internet side of gateway (reverse IP masquerading)
- Filtering on Internet side of gateway
- Routed by IP
- Filtering on LAN side of gateway
- NAT on LAN side of gateway (no operation).
- Packet delivered to LAN
For packets from the LAN to the Internet, the order is reversed. Following the diagram from right to left:
- Packet originates from LAN
- NAT on LAN side of gateway if Local NAT is enabled (optional)
- Filtering on LAN side of gateway
- Routed by IP
- Filtering on Internet side of gateway
- NAT (IP masquerading) on Internet side of gateway
- Packet sent on to destination on Internet
The Single Ethernet case is similar except that Local NAT is not available. Specifically, the instance of the Proxy module enabled for IP masquerading is now also processing packets between IP and the LAN. It does not translate datagrams to or from our "Private Network" so that IP masquerading will work correctly in this configuration. More information about NAT and Security is covered in the "Inbound Port Mapping" section.
Conclusion
Firewalls don't have to be complicated or expensive. A firewall is simply a mechanism for enforcing an access policy. The first step in choosing a firewall is to consider what access policies you wish to enforce. Using IPNetRouter, you can turn an existing Mac into a rock solid IP firewall---for a lot less $ than any other commercial hardware based firewall router.
Just remember: first BLOCK...then PASS (and you only have to enter PASS filters when you want to punch holes in your Firewall).
There's lots of information about "firewalls" available on the web. Visit your favorite web search engine for more information.
 Privacy
Policy
Privacy
Policy  Contact
Us
Contact
Us